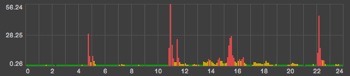
“There has been a 67 percent increase in overall spam volume and a 500 percent increase in image spam since Aug. 2006.”
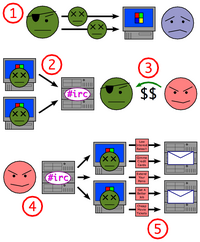 Illuminating (but seriously depressing) series of articles at eWEEK on botnets — arrays of 0wnz0r3d Windows computers assembled under the control of sophisticated “bot herders,” silently pumping every orifice of the interweb full of spam in all its forms. The virus that makes a machine part of a botnet does not cause harm to its host – like all successful viruses, it wants to assure its own survival. Amazingly, the latest generation of botnet software even installs antivirus software (a pirated copy of Kaspersky Anti-Virus, to be specific) to eradicate competing malware, so it can have the full resources of the infected host to itself.
Illuminating (but seriously depressing) series of articles at eWEEK on botnets — arrays of 0wnz0r3d Windows computers assembled under the control of sophisticated “bot herders,” silently pumping every orifice of the interweb full of spam in all its forms. The virus that makes a machine part of a botnet does not cause harm to its host – like all successful viruses, it wants to assure its own survival. Amazingly, the latest generation of botnet software even installs antivirus software (a pirated copy of Kaspersky Anti-Virus, to be specific) to eradicate competing malware, so it can have the full resources of the infected host to itself.
For a while, it looked like botnet activity was shrinking, but lately it’s seen a huge uptick. vnunet reports that a million-bot botnet is quietly being assembled around the world, and that we’ll soon see an even more massive onslaught of phishing and spam attacks.
The sophistication of these systems is amazing — the botnets even come with their own self-contained DNS system. “This allows a bot herder to dynamically change IP addresses without changing a DNS record or the hosting—and constant moving around—of phishing Web sites on bot computers.”
So can’t botnet hunters just focus on nailing the central command and control machines? Nope – that’s the “beauty” of using a peer-to-peer model:
Control is still maintained by a central server, but in case the control server is shut down, the spammer can update the rest of the peers with the location of a new control server, as long as he/she controls at least one peer.
One of the many factors that makes fighting back so hard is that infected bots expect incoming commands to be digitally signed. Commands from the bot herders to members of the botnet are securely encrypted, and virtually impossible to decipher or reverse-engineer.
The sophistication of modern spammers is impressive on so many levels. Image spam (e.g. Viagra ads that appear as graphics rather than text) has been especially vexing lately, as it seems to elude all filters. Since almost all anti-spam mechanisms — even collaborative ones like Akismet — rely to some extent on the ability to deduce unique “signatures” from a message, every single image sent by machines on a botnet has slightly different dimensions and characteristics, making it nearly impossible to nail down. I’ve even noticed random graphical noise splattered in the background of image spam lately – which prevents any two images from producing identical signatures.
I think I was wrong when I said recently that my IP firewalling script was becoming less effective because spammers had learned to spoof IPs. I believe now that the problem is that the botnets are so widely distributed that the same IPs don’t come up with enough repetition to be useful. Rather than spam spewing from a volcano somewhere in the Ukraine for a few days, it’s now more like a steady mist that suffuses the atmosphere – an endless acid rain emanating from everywhere at once.
What amazes me is that articles like this never seem to point out the obvious: The botnets are comprised entirely of Windows machines. There are currently approximately 5.7 million infected Windows computers out there, ready and able to join a botnet at any time. If I were the sysadmin of a Windows network, this would be significant information to me. It’s not that OS X or Linux are theoretically incapable of this kind of takeover, but the plain reality is that it doesn’t happen. And yet, articles like this never make a recommendation that admins consider a platform shift. Why?
Sadly, experts are starting to feel hopeless about their prospects of staying in front of the game.
We’ve known about [the threat from] botnets for a few years, but we’re only now figuring out how they really work, and I’m afraid we might be two to three years behind in terms of response mechanisms,” said Marcus Sachs, a deputy director in the Computer Science Laboratory of SRI International, in Arlington, Va.
Amazon is having serious issues with spam, as is del.icio.us. Of course one would expect large services to be constantly hammered with spam, but if the largest and best-funded commercial entities on the web can’t keep spam off their public doorsteps, you know things are getting serious out there.
It’s becoming increasingly popular for admins to block entire nations, either at the apache or at the firewall level. I’ve been tempted to do the same myself, but haven’t. Yet.
All of this applies to the interactive aspect of the web as much as it does to email. I deal with it on wikis, discussion boards, blogs, and apache logs (referrer spam). In recent months, I’ve seen them stuffing personal contact forms, and even the public jobs database at the j-school (which is absurd, since no job ever gets published without human review, but that doesn’t stop them from trying). Amidst all the Web 2.0 talk of participatory journalism, the wisdom of crowds, the read/write web, and two-way communication, it’s those very features that are being exploited by spammers and the massive botnets.
I worry that the openness that made the internet possible will ultimately become the sword upon which it impales itself. I see a future where everything is so locked down that all of the fun participatory stuff becomes impossibly difficult. I worry that someday email will only be feasible with whitelisting, that registration with identity verification will be required for all participatory web features, and that the concept of anonymity will ultimately become untenable.
Compare the atmosphere of the internet to the ecology of the earth. It took us millions of years to get to industrial civilization, then just a few decades to pollute our environment to the brink of sustainability. I worry that the internet is following a similar course – 30 years to become mainstream and five years to become so polluted it’s unusable.
Thanks Mal
Technorati Tags: botnets, spam



 Illuminating (but seriously depressing) series of articles at
Illuminating (but seriously depressing) series of articles at