Even the passwords we once considered “strong”  have become almost trivially easy for sophisticated crackers to break. With massive arrays of very-fast processors, lightning fast graphics cards, and extremely sophisticated cracking techniques, hackers are making mincemeat out of stolen password databases, and openly trading them on the black market.
Most “average user” passwords now fall so easily that some in the security community feel the username/password mechnanism itself must be traded in for something entirely different, like biometrics. But until that time comes, you need to be doing everything you can to make your passwords as secure as possible.

The purpose of this piece is not to scare you, but to give you the tools you need to stay safe.
There’s a ton of advice floating around out there on what makes for a good password, how to create memorable (and easy-to-type) passwords, and how to keep track of lots of different passwords. Unfortunately, a lot of that advice is written by geeks for geeks, while the people who generally need the advice the most are “regular” (non-geek) users. If you’re a geek, chances are you’re probably already doing most of this stuff. This article is an attempt to summarize the best password hygiene advice out there for your parents, bosses, aunts and uncles, and non-geek friends.
There’s a twist at the end, plus an explanation of the graphic above, so please read all the way through.
Password hygiene in a nutshell:
- Use strong passwords everywhere
- Never re-use passwords across different sites and services
- If #2 is not feasible, at the very least make sure your email password and your banking password are not used on any other site.
Let’s step through these points one-by-one.
Strong Passwords
A strong password is:
A) Long (12 characters or more – the longer the better)
B) Includes at least one each of lowercase and uppercase letters, at least one non-word typographic character like #, %, or ?, and a digit
C) Includes some character sequences that don’t appear in any dictionary in any language.
In other words:
32cMy.Little.Pony%17
is vastly more secure than
MyLittlePony
Because the latter consists entirely of character sequences that appear in dictionaries, and because it doesn’t include enough character types. By including only upper- and lower-case letters, each character can be one of 52 different characters. By including just one digit and one non-alphanumeric character, the cracker’s challenge is vastly amplified, since each character can then be any of those 52 plus 10 digits plus 33 symbols, e.g. one of 95 possible characters. The mathematics involved are exponentially more complex.
Sites requiring you to use one of each possible character type aren’t just being annoying – they’re being mathematically sensible.

Never, ever use a word that appears by itself in any imaginable dictionary, unaltered, as the entire password. And don’t think for a second that password crackers don’t use dictionaries in other languages – bad guys use consolidated dictionaries consisting of all languages! Your clever inclusion of French strings in your password isn’t buying you any safety.
A strong password is not necessarily hard to remember or hard to type! In the black art of password cracking, length is far more important than randomness. My.Favorite.Sch00l is actually a much stronger password than 3a.7b# (but see The Twist below).
Why are long passwords so important? Because when passwords are encrypted and stored, the encrypted value of every password stored in the system has the same length. Since the cracker doesn’t know whether your actual password is 13 or 14 characters long, s/he has to try all possible values in the 13-character namespace, and then all possible values in the 14-character namespace, and so on. Mathematically, the difference is astronomical. The longer your password, the more possible combinations have to be tried.
To gauge the strength of your passwords, try running them through the checker at Password Haystack (guaranteed safe and trustworthy). That site also has a good explainer on the reasons why length is more important than randomness.
Here are screenshots comparing the two sample passwords above to see how long it would take crackers to guess them, assuming an attempt rate of one hundred trillion guesses per second (see below on online vs. offline cracking scenarios).
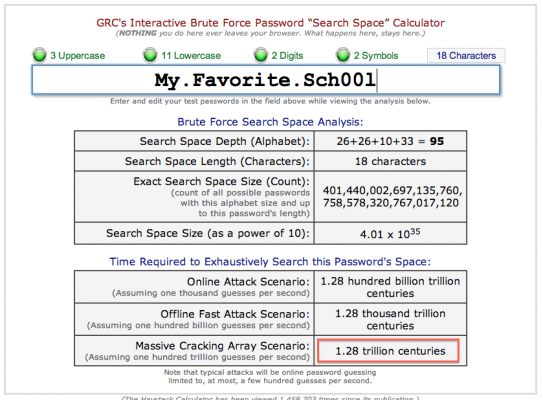
Compare the offline cracking scenario time estimate of the number in the red box to the one below (but again, read the twist at the end).

And fer godssake, please don’t use any of the passwords on the most-hacked lists.
Don’t Re-Use Passwords
A very common cracking scenario is that bad guys get into one of your services and then assume that, like most people, you use the same password on many different sites. More often than not, if they can figure out your password on one site, they’ve also figured out your password to other sites as well. Bingo – they’ve just gotten into all of your sites and services.
Password Managers
So if you can’t re-use passwords across sites, and if passwords need to be long and complicated to be safe, how in the world can you remember them all?
The only realistic answer is to use a “password management utility,” or password manager. There are a ton of them available for Mac, Windows and Linux, but they all work on the same principle: Maintain  a database of passwords attached to domains, all hidden behind a single master password.
The best password managers provide web browser plugins or extensions, so that when you visit a site and click the password manager’s browser toolbar button, all you have to do is enter the master password, and the long/complicated password is pulled out of the database and entered for you, matched to the domain.
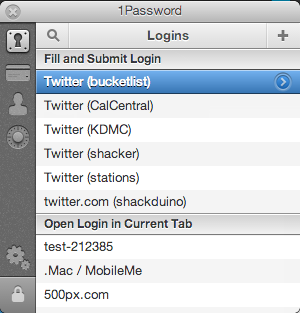
When I visit twitter.com and bring up the 1Password browser extension, it “magically” remembers all of the possible logins I might want to use on that site, even though all of the passwords are insanely complex and I remember none of them. I have almost 600 passwords stored in 1Password!
If you want to go “all the way” with complex passwords, a password manager gives you the freedom to set all of your passwords to 20-character, 100% random strings and not have to worry about remembering them or typing them in.
Many of us grew up in houses where we didn’t have to lock the doors when we left. Eventually, times changed and we started locking them. Or, we’ve gone from not needing a home alarm system to needing one. We adapted to meet changing security requirements in our environments.
Similarly, using a password manager is becoming a basic requirement of life on the intertubes. Yes, it’s a bit inconvenient at first, and is going to take some setup, but it’s also going to be one of those unfortunate but necessary changes that pretty much everyone will have to go through. Our children will take their necessity for granted.
There are a bunch of good password managers out there, but I’m personally a huge fan of  1Password. It’s a bit pricey, but it’s also the best. Identical on Mac and Windows, iOs and Android, 1Password also lets you store identity and credit card information (letting you fill out complex forms quickly), lets you securely store sensitive notes and file attachments, is taggable and searchable, provides extensions for all major browsers, lets you store software serial numbers, and has a great interface.  If you want your passwords to stay synchronized across multiple computers and devices, 1Password will let you do that via Dropbox. Worth $50 in a heartbeat, IMO.
Note: None of the good password managers store passwords on their own sites – even if the 1Password site were cracked one day, there would be no password databases there for the attackers to discover.
The Most Important Password of All
People tend to say “I don’t keep secrets in my email so I don’t need a strong or unique password for that.” But think for a moment: When you forget a password to some site or service, and do a password reset, where does the new password get sent? To your email address! Therefore, if the attacker can get into your email, they can probably get into ALL of your sites by requesting password resets – from Facebook to your favorite forum to your online bank account. Your email address is the KEY to your entire kingdom. Your email password MUST be strong and unique.
If you follow little of the advice above, at least follow this:
Make sure your email password is strong and unique, and don’t re-use it on any other site.
Online vs. Offline Attacks
There are two ways a cracker can try to guess your password:
1) Online: By using a program or script to attempt to enter guessed passwords into some website. But a well-buit site will notice lots of bad attempts and throw roadblocks in the attacker’s path, such as image-based captchas. They may even add the attacker’s  IP address to their firewall, blocking them entirely.  Assuming you use a strong password, and assuming that the cracker hasn’t obtained your password some other way, it unlikely (though not impossible), that an attacker will be able to run through enough password guesses to hit yours without being blocked first.
 2) Offline: But what if the attacker could get ahold of a site’s entire database of stored passwords? Â Then they could attempt their guesses at a rate of billions of attempts per second (not kidding!) on their own computers instead of against the web server, without any roadblocks in their way.
2) Offline: But what if the attacker could get ahold of a site’s entire database of stored passwords? Â Then they could attempt their guesses at a rate of billions of attempts per second (not kidding!) on their own computers instead of against the web server, without any roadblocks in their way.
Sounds far-fetched, but sadly and unfortunately, that’s just what has happened at dozens of popular sites over the past few years. Sophisticated hackers have found their way into high-profile sites, stolen their password databases, and published them online. In the past year, LinkedIn and Evernote users have received confessional emails from those sites requiring them to reset their passwords after their databases had been breached.
Once published, crackers  download the databases to their own computers and have a field day, throwing every trick in the book at the lists with ultra-high-speed clusters of CPUs and graphics cards (which are awesome at solving mathematically hard problems). Their success rates are both shocking and sobering, approaching 90% in some cases.
The Twist
Much of the advice above assumes that attackers are working on a purely “brute force” basis – computationally trying mathematical combinations until they hit paydirt. That assumption is why advice like “Take your favorite album title and replace the spaces between the words with punctuation marks” or “String together the street address of the house you grew up in with your pet’s name and throw in some digits and periods” used to be pretty good advice – they get you a nice, long, memorable password that’s still relatively easy to type.
Unfortunately, that advice could also lull you into a false sense of security.
The anatomy of a hack piece at Ars Technica is pretty dense, but one of the big take-aways is that brute force techniques are only part of the modern password cracker’s arsenal. They also use amazing pattern-matching techniques, in all kinds of mix-and-match combinations. Even though passwords like “Coneyisland9/” or “momof3g8kids” look pretty good on the surface, and even though they’re not included in any dictionary, the crackers in the competition were able to break them anyway.
While those passwords are much better than simple / unadorned dictionary words, they still fell at the hands of expert crackers using a combination of brute force and pattern mixing techniques. The lesson? If you want to be as safe as possible from serious off-line attack scenarios, follow the advice of one of the commenters at the end of the piece:
“You can’t use ANY rule to create passwords. Your passwords MUST BE RANDOM. No rules, no “clever” tweaks, nothing. Random. Anything one human can think of, another can. We’re pretty dumb that way. Passwords must be random.”
At the end of the day, your password safety exists on a spectrum. Using any of the techniques above is better than using none at all, and using several of them is better still. For the best possible security, use fully random, very long passwords that are never re-used between sites. And the only way to do that is to use a password management utility.
The fly in the ointment with that plan is that the password manager browser plugins don’t generally  work on the iOS/Android browsers. If you’re a heavy mobile user, the fully random approach isn’t going to work for you – best to stick with passwords that are long and include all character sets, but that are still memorable and type-able.
As for that “correct horse battery staple” image at the top, see the famous xkcd comic it references.

Thank you so much, Scot. Very helpful.
Thanks Scot. I’ve shared this on my Facebook feed. I don’t like to harp about security but when I find a good article that speaks in common-folk language, I pass it along. Little-by-little, I can only hope to gently educate my friends about how to incrementally safeguard their online activities. This post fits the bill perfectly.
So glad you found it useful Amwas! Thanks for passing it along.
Just FYI (and my apologies for not crediting you as today’s inspiration. But, to be honest, I post security-related stuff like this quite often. If it hadn’t been your post, I’d’ve likely soon been inspired to share by another, similar post.
‘sall good, Man!)
https://www.facebook.com/photo.php?fbid=737511636274888&set=a.100111603348231.22.100000481740378&type=1